Hackers and pirates use VPNs, Tor and Proxy Networks
Each year, hundreds of courses are stolen by students using VPNs, Tor or proxy networks. These tools allow them to remain anonymous and can cost thousands of dollars in lost revenue.
Each year, hundreds of courses are stolen by students using VPNs, Tor or proxy networks. These tools allow them to remain anonymous and can cost thousands of dollars in lost revenue.
By using enterprise grade network monitoring, we can detect 99% of all VPNs in use in the world today. These networks can allow course thieves to operate anonymously but with our software you will quickly unmask them.
“VPNs were used in the majority of the thefts I experienced as a course creator. Since disabling VPN access to my school, I've never had a problem.”
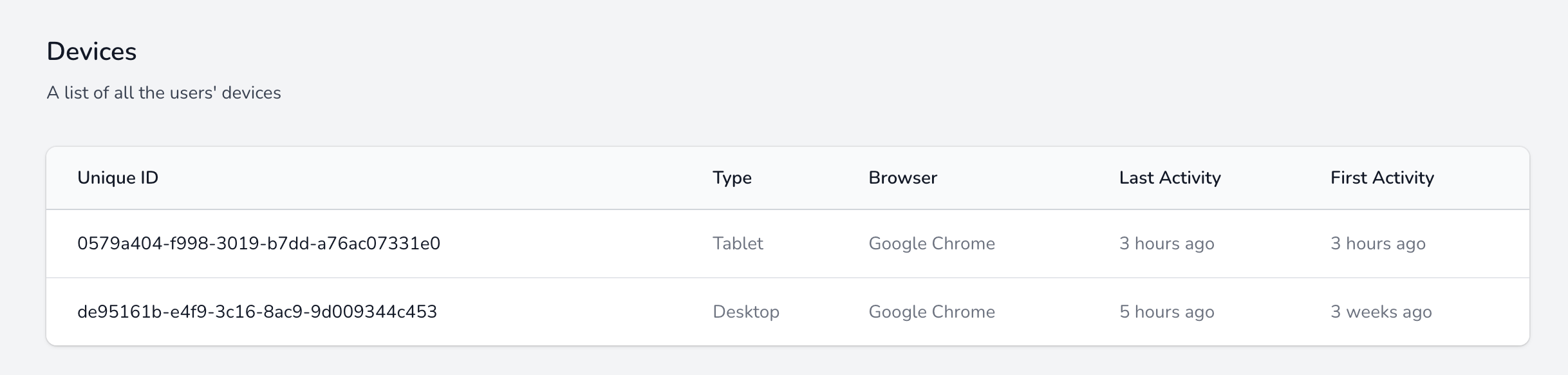
When using our software, you can be rest assured that your students are fully traceable and your content is safe.

Our software was designed from the ground up to be easy to use and deliver value from the moment of installation. No complex set up or dashboards.
Whether you are teaching 10, or 10,000 students, our software can protect your content.
Need to delegate? You can allow managers and course administrators to monitor on your behalf.
Our sofware can connect to Zapier, Automate.io and countless others to automate your workflows.
When a user breaks a rule, our system will instantly notify you by email. We also support Slack, SMS and others.
Need to stop access from a country or region? Or only teach in the EU? Our system can alert based on the students location.
Prevent impersonation and obscurification attempts through the use of VPNs, Tor and Proxy Networks. Our system can detect and notify you, instantly.
Our systems are encrypted at rest and between your course and our servers. This ensures the highest level of privacy and security.
Our system is designed to keep you compliant with GDPR and other data processing regulations.