Fake emails are where pirates hide
By using a fake or disposable email, students can access your content anonymously often with the intent to steal or copy it.
By using a fake or disposable email, students can access your content anonymously often with the intent to steal or copy it.
Using cutting edge technology we can reliably and accurately detect fake and disposable emails, meaning you can be assured your students are using real email addresses when accessing your content.
“All of my chargebacks, and fraudulent orders, have been from students that used a disposable email when signing it. It cost me hundreds of dollars.”
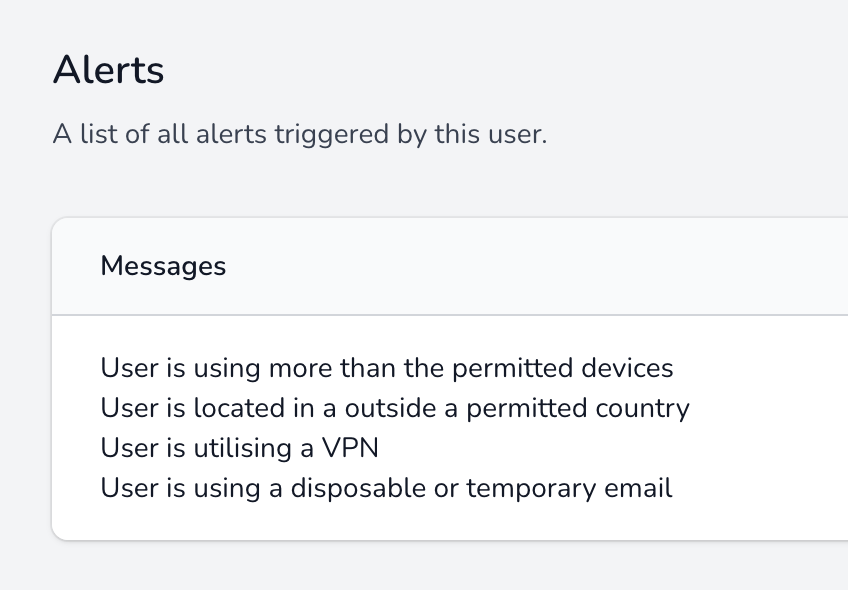
With a genuine email address, your legal team has a head start in pursuing a student for infringement. Fake and disposable emails have no paper or digital trail for your team to follow.

Our software was designed from the ground up to be easy to use and deliver value from the moment of installation. No complex set up or dashboards.
Whether you are teaching 10, or 10,000 students, our software can protect your content.
Need to delegate? You can allow managers and course administrators to monitor on your behalf.
Our sofware can connect to Zapier, Automate.io and countless others to automate your workflows.
When a user breaks a rule, our system will instantly notify you by email. We also support Slack, SMS and others.
Need to stop access from a country or region? Or only teach in the EU? Our system can alert based on the students location.
Prevent impersonation and obscurification attempts through the use of VPNs, Tor and Proxy Networks. Our system can detect and notify you, instantly.
Our systems are encrypted at rest and between your course and our servers. This ensures the highest level of privacy and security.
Our system is designed to keep you compliant with GDPR and other data processing regulations.